Secure hardware and software for network challenges
A discussion of the Industrial Internet of Things (IIoT) and security must embrace a networked system, but it must also be cognizant of the controllers and gateways involved, the cloud and even remote mobile handheld devices. Essentially, securing the infrastructure means allowing things that are supposed to happen and preventing those that are not. Today’s IIoT presents some different challenges than the typical information technology (IT) server environment. An IIoT network is comprised of many connected devices.
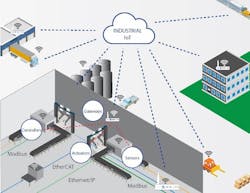
Because the IIoT is evolving so quickly, more intelligent gateway and edge devices are needed that are rooted in a comprehensive end-to-end security strategy. Courtesy of Mentor Graphics.
Devices are not locked up in a server room within a secure perimeter, where only IT staff has physical access to them. Instead, these connected electronic devices can be spread throughout large geographical areas to engage in sensing, collecting, reporting, managing, processing and interpreting data (see Figure 1).
Many of these devices are available on the open market, so a malcontent or hacker could obtain a device to hack or reverse engineer it, meaning any system using that device is vulnerable to a dangerous set of threat vectors.
As an industrial business operation that is either building or managing an IIoT network, it is crucial to realize that device communications must be secure, and so must the device itself.
At a basic level three fundamental principles should be considered to ensure the protection and security of an IIoT network: protect the data, secure the communication and enable visibility.
Data protection & hardware-enforced security
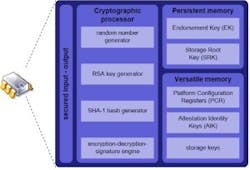
Protecting data is both a hardware and a software issue. Many of the most secure techniques are rooted in finding the devices that leverage the right security-enabled hardware. Numerous hardware security modules are available from suppliers that include silicon vendors with a sophisticated and robust set of capabilities, as well as low-cost solutions having only a subset of these capabilities (see Figure 2).
Figure 2. HW security features to look for include: security module, cryptographic processor, secure key/certificate storage, isolation of security-related tasks and support for chain of trust. Courtesy of Mentor Graphics.
Important hardware security features include cryptographic capabilities and accelerators. Hardware should include a random number generator to ensure generation of strong cryptographic keys. If the device does not include this in the silicon, embedded devices will find it difficult to generate unique keys to ensure each device has a strong, random key that makes it difficult for hackers to compromise.
A lack of random number generator or strong keys is often the single cause of major security breaches. Hardware implementations can be trusted, but software implementations are sometimes weak or not aligned with the underlying capabilities of the hardware.
In some high-profile cases, software programs were used to encrypt data on a drive. Instead of storing encrypted data deep within the hardware, the root key for decrypting everything was in a plain text file, leading to a very easy compromise or exploitation.
A hardware security module protects secrets. Hardware-based key storage means no one can access the security keys or crypto keys without proper permission or authorization.
For example, ARM TrustZone technology allows separation of code and devices into two different universes. One set is partitioned into protected memory space known as the "secure world." The rest runs in another memory space in the "normal world" where normal user applications are run. All critical operations run in the protected or secure world, and all storage and elements that require access to certain certificates and private keys also reside in that space. With this system, software architects and developers can separate device resources and assign what activity goes where. If a resource in the normal world is infected, the malicious code will not spread to the more valuable code in the secure world.
Software-enabled security
A security framework that enables quick and easy build-out of the system with robust security features is essential. Ideally, a software security framework is built on top of a hardware security module. Even without the necessary hardware, a software development team can still implement key capabilities and emulate parts of the hardware pieces in software as an interim solution until the next level of hardware is introduced into the IIoT system.
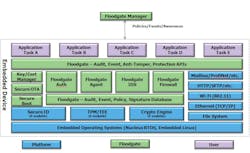
Figure 3. The security framework includes embedded software building blocks from Mentor Graphics (blue), security features from Icon Labs (green) and room to customize for each individual application (purple). Courtesy of Mentor Graphics.
Figure 3 provides an architectural view of an embedded security framework tailored exclusively to IIoT devices. It was built from the ground up to run on devices that require a Real-Time Operating System (RTOS) or Linux and to solve many of the issues around embedded security – as opposed to a large IT solution retrofitted into an IIoT device. With it, software developers can utilize secure boot, secure remote firmware updates, and manage keys and certificates. The Floodgate components from Icon Labs allow users to detect events, report events, update policies and handle other security related events.
The framework’s scalability provides basic foundational security on tiny devices such as sensors or actuators that are built on small, low-power eight-bit microcontrollers. On larger, more complex devices, the framework easily scales to add more capabilities.
Finally, many IIoT network managers approach building the network piece by piece and believe it is more economical to build a custom IIoT network from the factory floor up through the infrastructure. This strategy becomes problematic when engineers and integrators use pieces of software and components together to configure, manage, and integrate them. Productivity and hours would be lost if unforeseen situations occur.
Securing the communication of an IIoT network
Securing communication and the right security protocols such as IPsec, SSL and TLS are important to securing an IIoT network.
Additionally, authentication is often overlooked. A typical implementation often uses one-way authentication where one of the parties in the communication validates the other. Using the IT model again, a client Web browser validates the server that it is talking to, but it does not authenticate the other way to the client.
Accordingly, an IIoT system in which all the devices are able to authenticate each other is critical to a successful and secure environment. To do so, a system can extend the certificate-based public key infrastructure that is common on the Internet to ensure its capability supports machine-to-machine authentication.
In fact, certificates within IoT and embedded devices enable code signing, which is important for secure boot or remote software updates. Secured certificates can also be used for mutual authentication, ensuring safe and secure transmission.
Managing a device and enabling visibility
Unfortunately, in the world of industrial internet, hackers can find devices, probe them and potentially get in. If they can’t get in easily, they can sit and keep trying over and over again – and the device under attack may never know. Most devices today cannot recognize if something abnormal is going on. They do not have enough intelligence to even detect a problem, let alone report it.
One solution is to build an embedded firewall into these devices to control the access. With it, the team can control what IP addresses, ports and protocols are open. Other capabilities, such as stateful packet inspection, threshold filtering and protocol-specific deep packet inspection, can be added for the specific device.
Many embedded devices operate in very static environments. In a factory where the device talks to a known set of devices, it is easy to lock down what is supported and detect changes, oftentimes referred to as "white listing." If a new device shows up in the IIoT network, an alert can be generated.
The bottom line is that if a device is detecting anomalous behavior, it needs to be able to report it so that an IIoT network administrator can take action. Security updates and patches need to be sent out to the infected areas immediately.
The emergence of the intelligent gateway
Last year Gartner published a study stating that 5.5 million new things are connected online every day. It predicted that by the end of 2016, 6.4 billion devices will be connected, and by 2020, that number will grow to 20.8 billion.
With all these connections more data is flowing through the IoT and IIoT networks. Machine intelligence in industrial environments is being pushed from the cloud toward the edge. The result is the need for more intelligent and customizable gateways and edge devices. In addition, with exponentially increasing amounts of data now being stored in edge devices and gateways, a much more comprehensive security strategy is needed, especially for the gateway because this device serves as the aggregator, manager and facilitator.
Figure 4. The Mentor IoT gateway SysDK reference design can be used
in its current form or customized to meet specific gateway hardware and software requirements, including compatibility with legacy infrastructure and new IIoT deployments.
An IoT system development kit’s hardware and software are customizable (see Figure 4). It addresses the intelligent gateway market by meeting gateway functional requirements. With hardware and software customizable as to connectivity options, it can be tailored to support the integration of both brownfield and greenfield devices.
The gateway software includes drivers and firmware. It can be configured to include the Nucleus RTOS as well as Mentor Embedded Linux, a security framework, and also includes support for ARM TrustZone and any of the legacy and new connectivity types found in a typical factory or plant.
Businesses can use this customized platform to build applications that meet the necessary requirements of an enterprise.
Conclusion
The IIoT brings a complex set of challenges to the forefront. Security is needed everywhere. Devices are everywhere. Even with a secure perimeter, people have found ways to break into it, so solutions must be sought that integrate security intrinsically within the entire industrial complex.
IIoT security is too complex for an IT department to go out and try a few building blocks here and there. Ideally, IT can partner with parties who have end-to-end capabilities in both hardware and software and existing integrations in place. With that, a company can place its network – and the way it does business – one step ahead of the game.
Warren Kurisu is the director of product management in the Mentor Graphics Embedded Systems Division, where he oversees the embedded runtime platform business for the Nucleus RTOS, Mentor Embedded Linux, virtualization and multicore technologies, safety certified runtimes, graphics, and development tools. He has spent nearly 30 years in the embedded industry. Kurisu holds a master’s degree in electrical engineering from the University of Southern California and a Master of Business Administration from the University of California at Berkeley.